Automatic Parameterization of CSRF Tokens
CSRF token is a special token used by some servers to prevent the Cross-Site Request Forgery (CSRF) attacks. It is
a random number which is different in each new session.
The attacker is not able to guess the token and create a valid request. If the server uses CSRF tokens, it does not accept
requests with the wrong token (or no token).
There are several ways to transfer CSRF tokens in the server response:
![]() In the header of server response
In the header of server response
![]() In the body of server response
In the body of server response
![]() As a cookie value
As a cookie value
WAPT Pro can find any of these CSRF tokens in the server responses and automatically parameterize them.
Let's see how it works.
During recording WAPT Pro searches for request header X-CSRF-TOKEN.
You can see it on the "Request Header" tab of "Response processing". This header has a certain value:
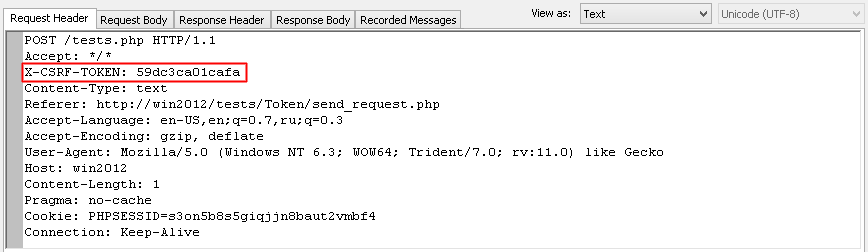
It is the value of CSRF token.
WAPT Pro extracts this value and searches for it in the server responses to all previous requests.
The search is done in response headers, bodies and cookies.
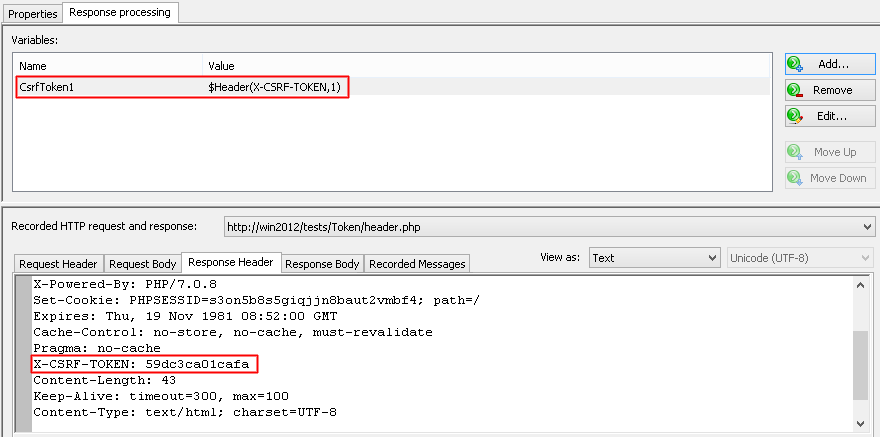
- CSRF token is found in the header of server response
If WAPT Pro finds the token value in the header of server response, it creates a variable which uses the $Header function:
- CSRF token is found in the body of server response
If WAPT Pro finds the token value in the body of server response, it creates a variable based on the $Search function. This function uses the left and right boundaries of the found value:
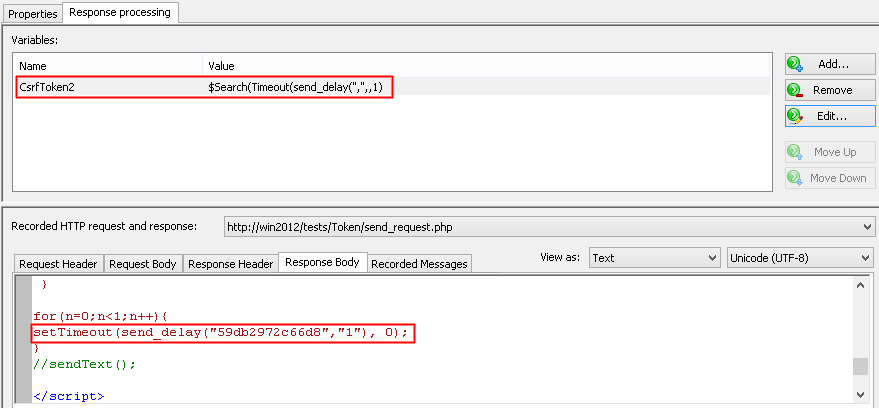
During the test this function will search for the value surrounded by the same boundaries in the body of server response, and variable will get the actual token value.
- CSRF token is set as a cookie value
If WAPT Pro finds the token value set as a cookie value, it creates a variable which uses the $Cookie function:
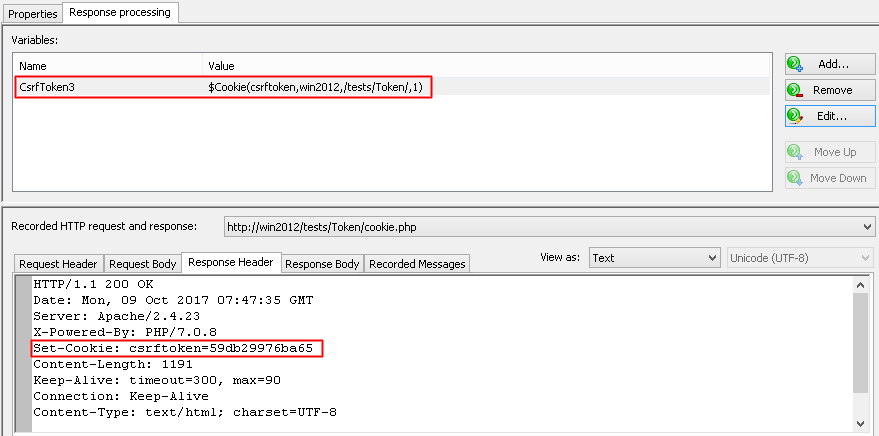
In all these cases
created variable is substituted in the X-CSRF-TOKEN header of request where the token value was initially found:
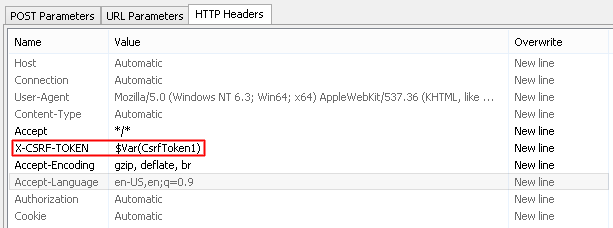
During the test the X-CSRF-TOKEN will get the actual value expected by the server.
